Pingpong
This is a writeup of the Forensics challenge pingpong by swampCTF
Points: 53
Premise
What happened to my traffic??? The pings?!?? They’re taking over!!!! They’re… ping… pong pingpong ping find my pong flag.
Challenge files:
Observations
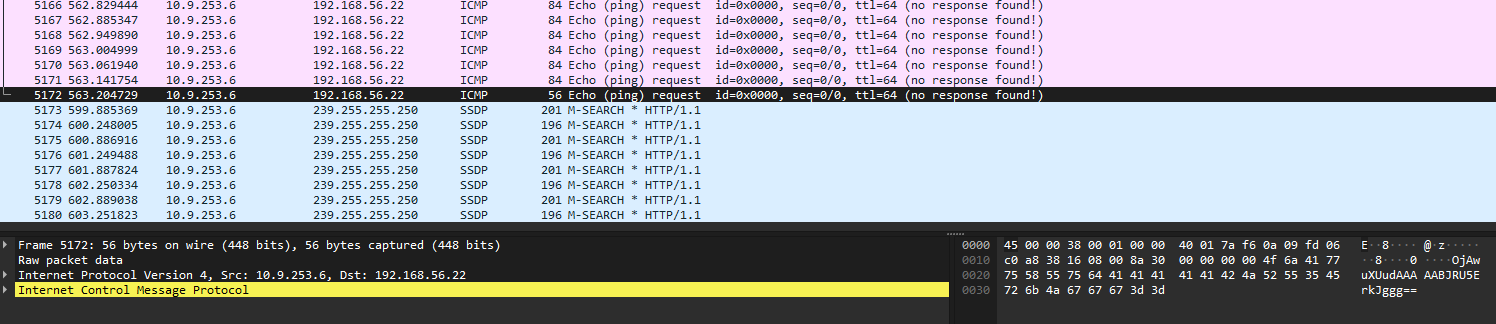
Opening the file, we saw a lot of pings, but the data didnt seem to comprehensible at first, but scrolling down a bit, I found the following:
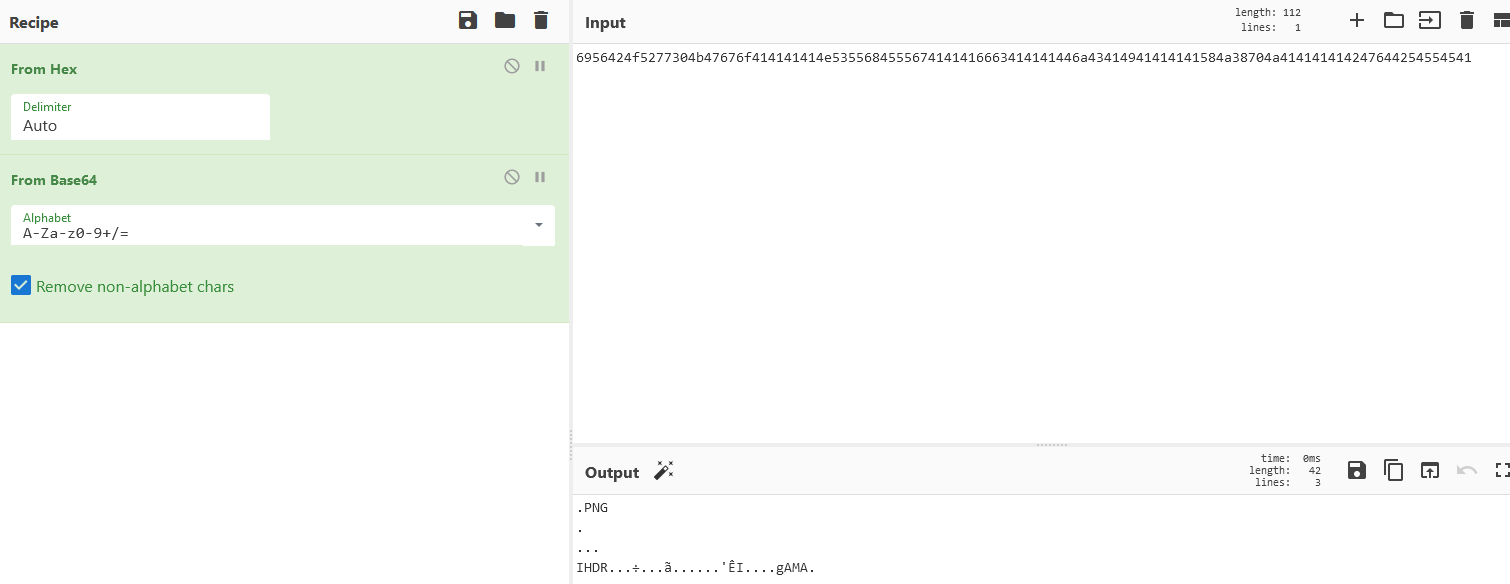
Which looks an awfull lot like base64 encoded data, so I go back to the first package, and try to base64 decode it using Cyberchef, and see the following:
Solution
So, we know we have a few ICMP packets that we need to extract the data from, decode from base64, and render as an image. To do this, the first thing I do is to save the packets as json data, and name the file icmp.json followed by writing this python script:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
import json
import base64
import io
import PIL.Image as Image
with open('icmp.json') as f:
data = json.load(f)
#We're after _source -> layers -> icmp -> data -> data.data
img_str = ""
for i in data:
#print(i.get("_source").get("layers").get("icmp").get("data").get("data.data"))
img_str += i.get("_source").get("layers").get("icmp").get("data").get("data.data")
the_str = img_str.replace(":", "")
#print(the_str)
hexbytes = bytes.fromhex(the_str).decode('utf-8')
#print(hexbytes)
b64_decoded_str = base64.b64decode(hexbytes)
#print(b64_decoded_str)
img = Image.open(io.BytesIO(b64_decoded_str))
img.show()
This extracts the image and shows us the following: 
So now we have the flags:
swampCTF{d474_15_3v3rywh3r3}