New C2 Channel
This is a writeup of the Forensics challenge New C2 Channel? by swampCTF
Points: 125
Premise
Sometimes you can exfiltrate data with more than just plain text. Can you figure out how the attacker smuggled out the flag on our network?
Challenge files:
Observations
Upon opening the file in wireshark, I inspect the first HTTP packet, and see the following 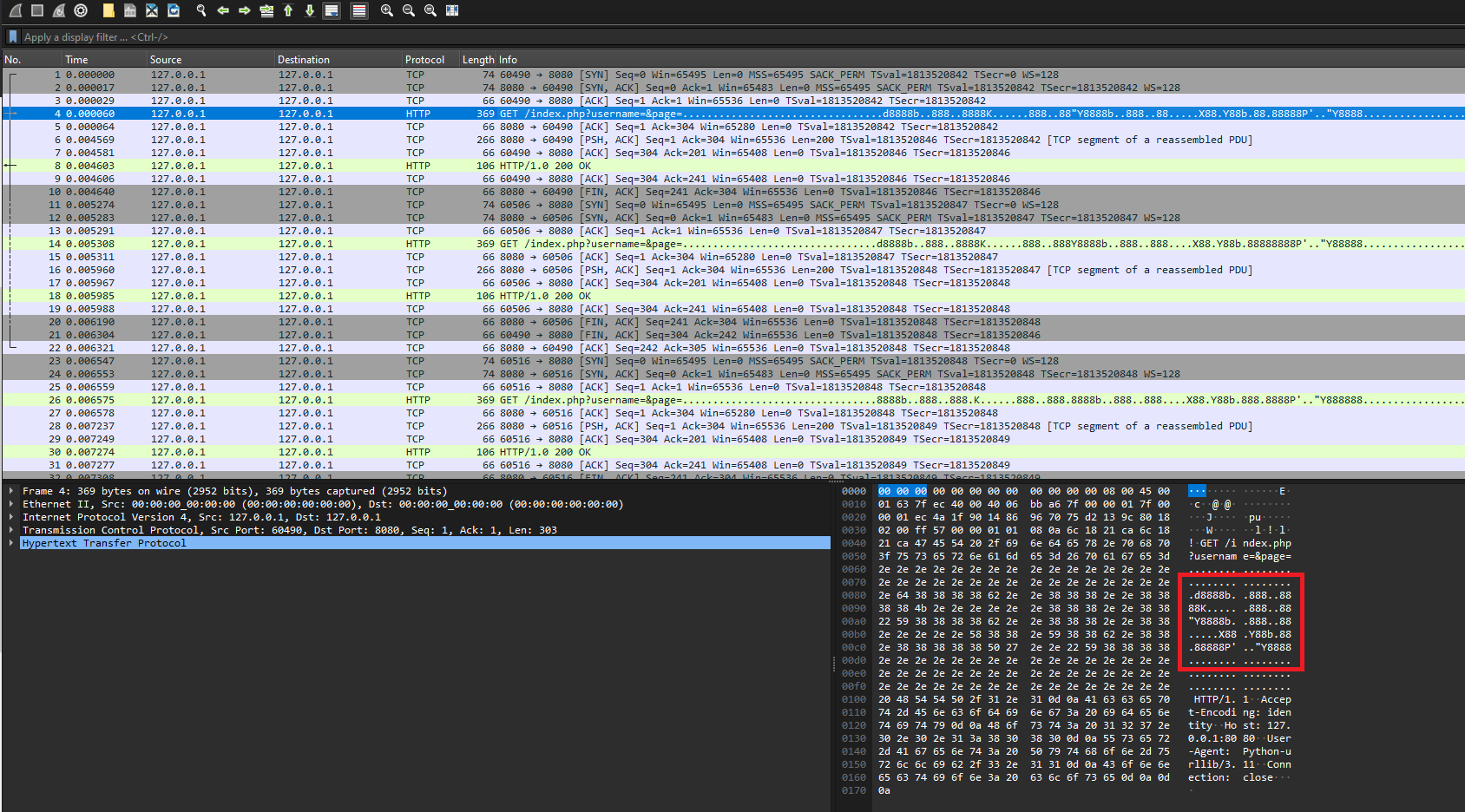
Which looks a lot like a ascii art s and part of another character.
Solution
Following the http packets with the string username slowly prints out the flag in ascii format 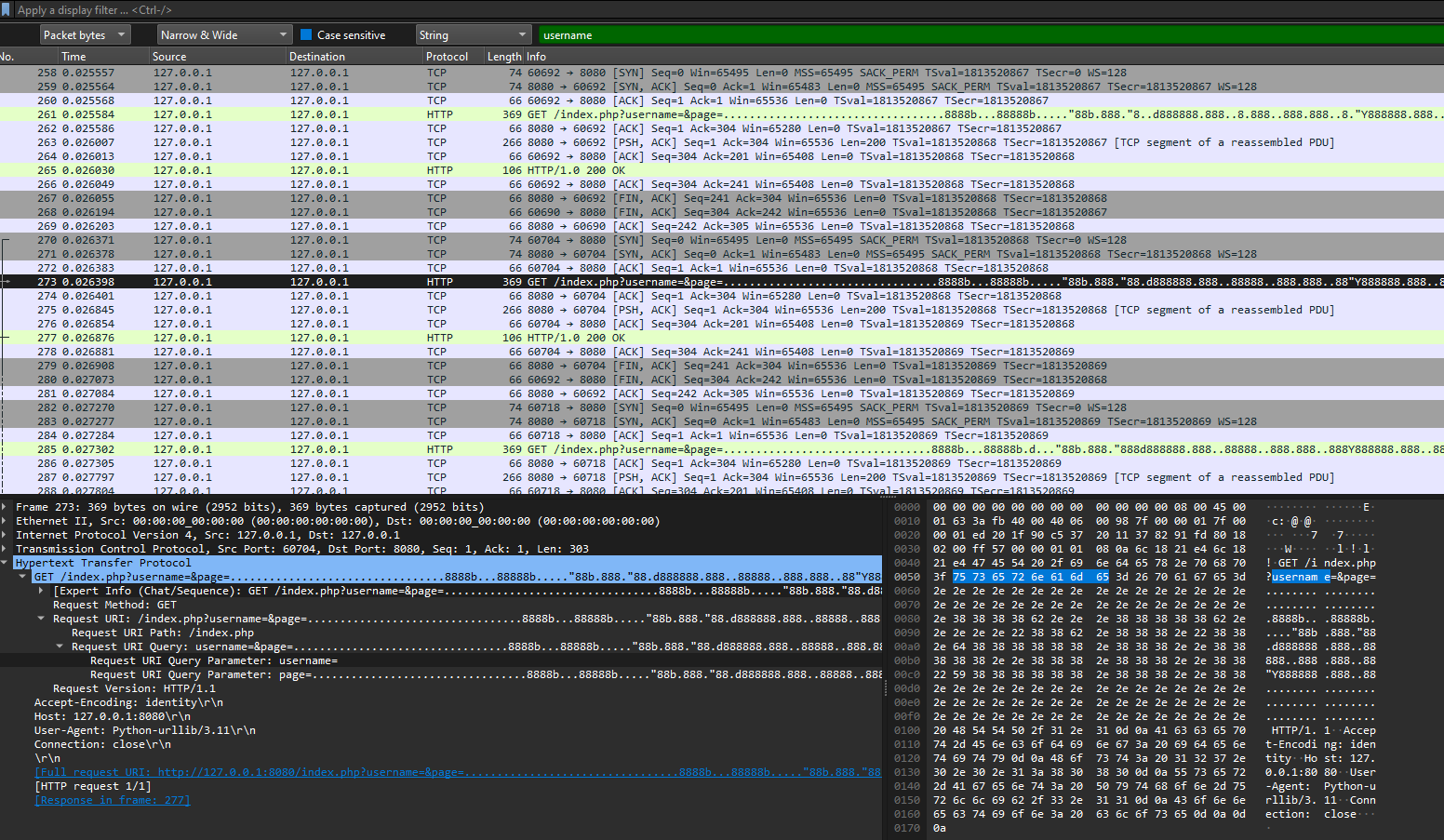
This slowly builds the flag:
swampCTF{w3lc0m3_70_7h3_l4nd_0f_7h3_pc4p}
Tools and sources used:
This post is licensed under CC BY 4.0 by the author.