Rabid
This is a writeup of the crypto challenge Rabid from the TFC CTF
Points: 50
Premise
There might be a little extra piece of information here.
Challenge chiphertext:
VEZDQ1RGe13kwdV9yNGIxZF9kMGc/IT8hPyE/IT8hPi8+Pz4/PjEyMzkwamNhcHNrZGowOTFyYW5kb21sZXR0ZXJzYW5kbnVtYmVyc3JlZWVlMmozfQ==
Observations
When viewing our encoded string, we can see that we’re dealing with a base64 string.
- (Note: If you want to be extra sure, you can use a tool like dcode.fr)
When decoding the string, we find it to only be partially decoded, since we can identify the TFCCTF{ piece of the string. 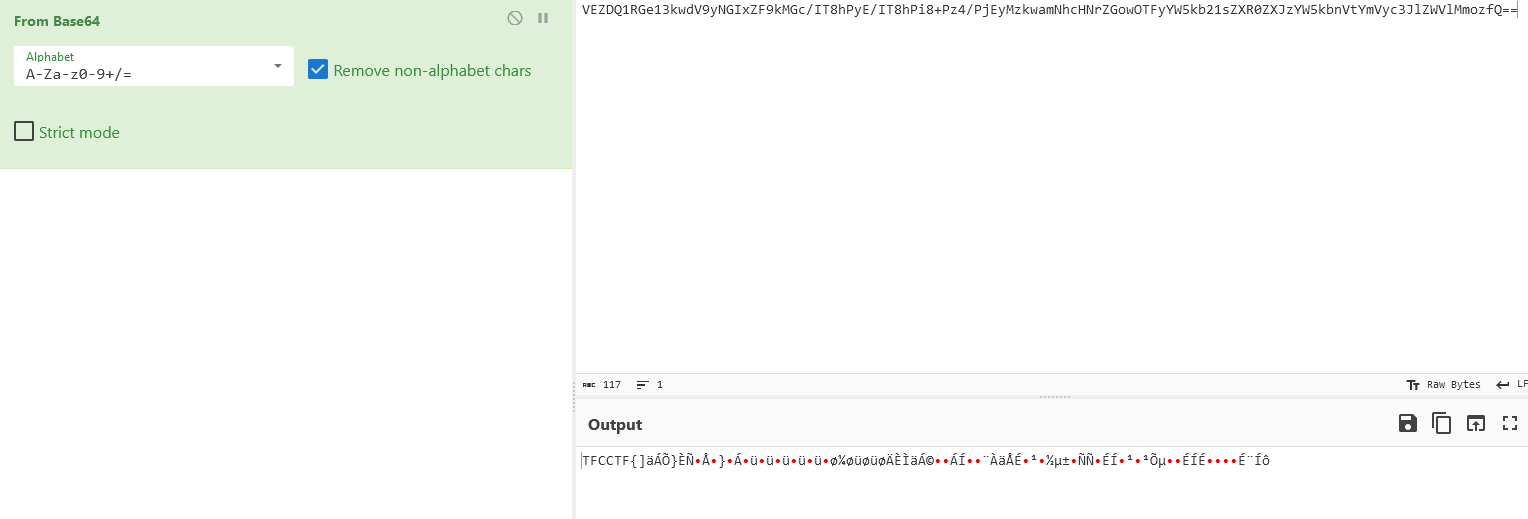
Solution
If we walk to the part of the string that starts after the TFCCTF{ part of the encoded string, we can see if changing the string by for instance removing a character changes the result, so we remove the 1 from the VEZDQ1RGe13kwdV9yNGIxZF9kMGc portion of the string. This gives us the following result, containing the flag: TFCCTF{y0u_r4b1d_d0g?!?!?!?!?!>/>?>?>12390jcapskdj091randomlettersandnumbersreeee2j3} 
Tools and sources used:
- (Optional) dcode.fr
- https://gchq.github.io/CyberChef