Samurais Code
This is a writeup of the Forensics challenge Samurai’s Code by apoorvCTF
Points: 162
Premise
Unveil the lost code of the Samurai and unlock the mystery hidden within.
Challenge files:
Observations
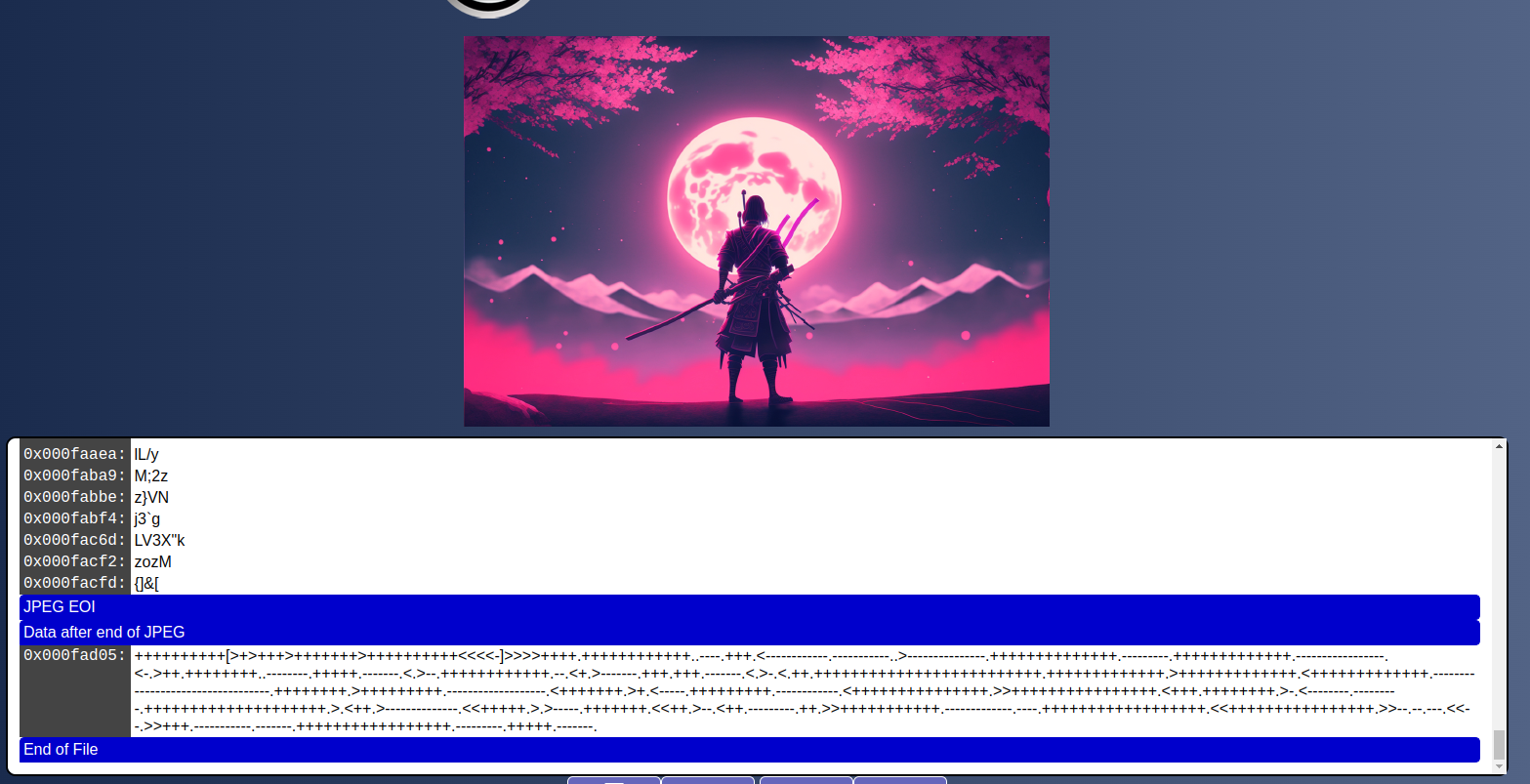
We start off by looking at the challenge image: 
Nothing seems out of the ordinary from the image, so we need to start investigating a bit further. Exiftools didnt yied anything of interest, but we can continue to the site Fotoforensics
Here we can see what looks a lot like Brainfuck at the end of the image.
++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>>>++++.++++++++++++..----.+++.<------------.-----------..>---------------.++++++++++++++.---------.+++++++++++++.-----------------.<-.>++.++++++++..--------.+++++.-------.<.>--.++++++++++++.--.<+.>-------.+++.+++.-------.<.>-.<.++.+++++++++++++++++++++++++.+++++++++++++.>+++++++++++++.<+++++++++++++.----------------------------------.++++++++.>+++++++++.-------------------.<+++++++.>+.<-----.+++++++++.------------.<+++++++++++++++.>>++++++++++++++++.<+++.++++++++.>-.<--------.---------.++++++++++++++++++++.>.<++.>--------------.<<+++++.>.>-----.+++++++.<<++.>--.<++.---------.++.>>+++++++++++.-------------.----.++++++++++++++++++.<<++++++++++++++++.>>--.--.---.<<--.>>+++.-----------.-------.+++++++++++++++++.---------.+++++.-------.
Running the code using dcode.fr, we get the following output: 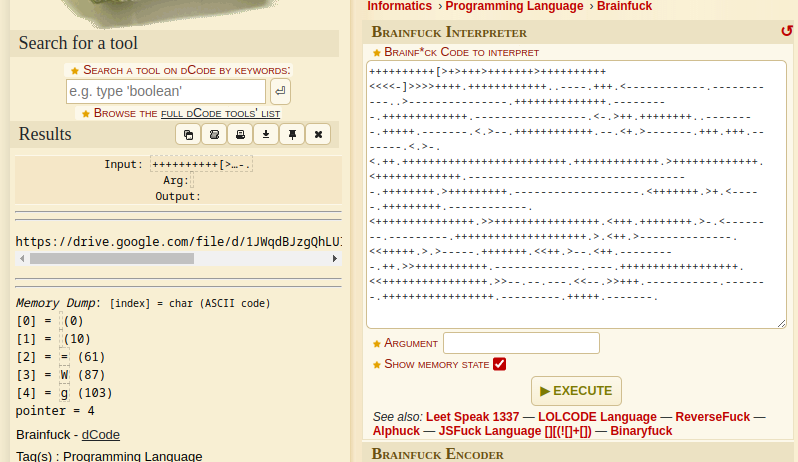
We get this link to a google drive, navigating to it we can download a file simply titled samurai.
Opening the file, we see what looks like a jpg with its bits shuffled 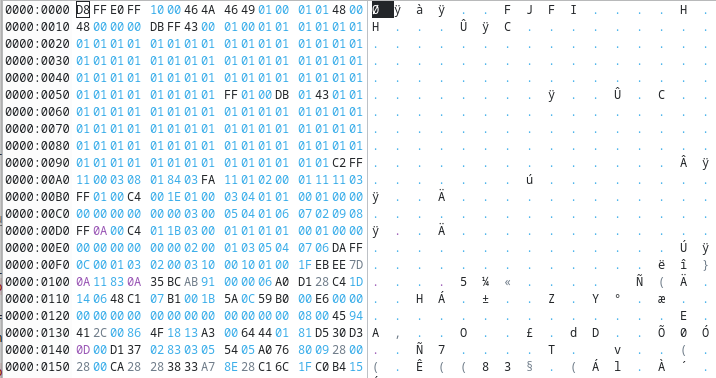
as according to the JPEG file format, we should see the first bytes be FF D8 FF E0
Solution
All we need to do to recover the bit shuffled image is shuffle them back, which we can do with the following python script:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
def shift_bytes(file_path, output_path):
with open(file_path, 'rb') as f:
data = bytearray(f.read())
for i in range(0, len(data) - 1, 2):
data[i], data[i + 1] = data[i + 1], data[i]
with open(output_path, 'wb') as f:
f.write(data)
print("Bitshifting complete")
input_file = 'samurai'
output_file = 'shifted_samurai.jpg'
shift_bytes(input_file, output_file)
The result is the following image: 
Which gives us the flag:
apoorvctf{ByT3s_OUT_OF_ORd3R}
Tools and sources used:
- Fotoforensics
- dcode.frs brainfuck site
- A hex editor of choice
- the JPEG file format