List
This is a writeup of the forensics challenge LIST from the TFC CTF
Points: 50
Premise
Who knew RCE was this useful?
Challenge file:
list.zip unzips to contain list.pcap
Observations
Analyzing the traffic, we can determine that some filtering is going to be required.
After a while of tweaking, I found the most useful data to be in HTTP POST requests, except for 2 where they were not needed, so they got filtered out as well. Ultimately this was the filter we ended up with: !ocsp && http.request.method == POST and !(tcp.stream eq 185) and !(tcp.stream eq 186) Which gave us the following traffic as a result: 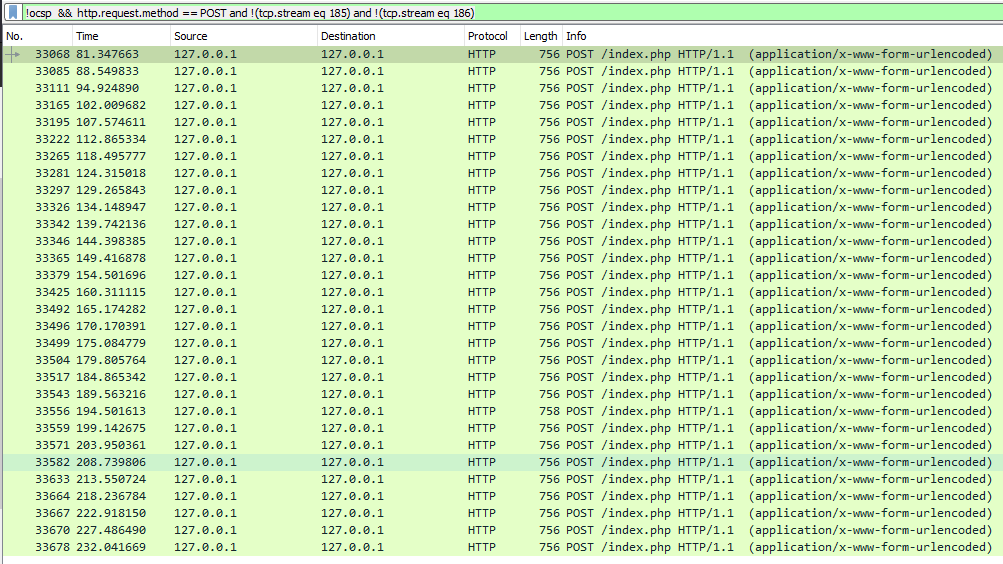
Solution
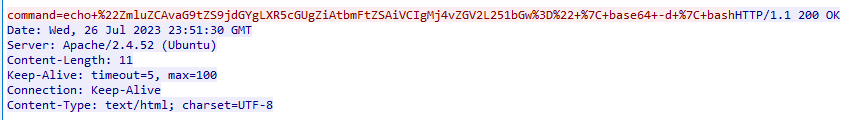
Following these HTTP streams gave us several different strings that looked to be base64 encoded.
We can also trim off some excess from the strings themselves, so we only decode the actual base64 string. Doing this gives us lines like the following: 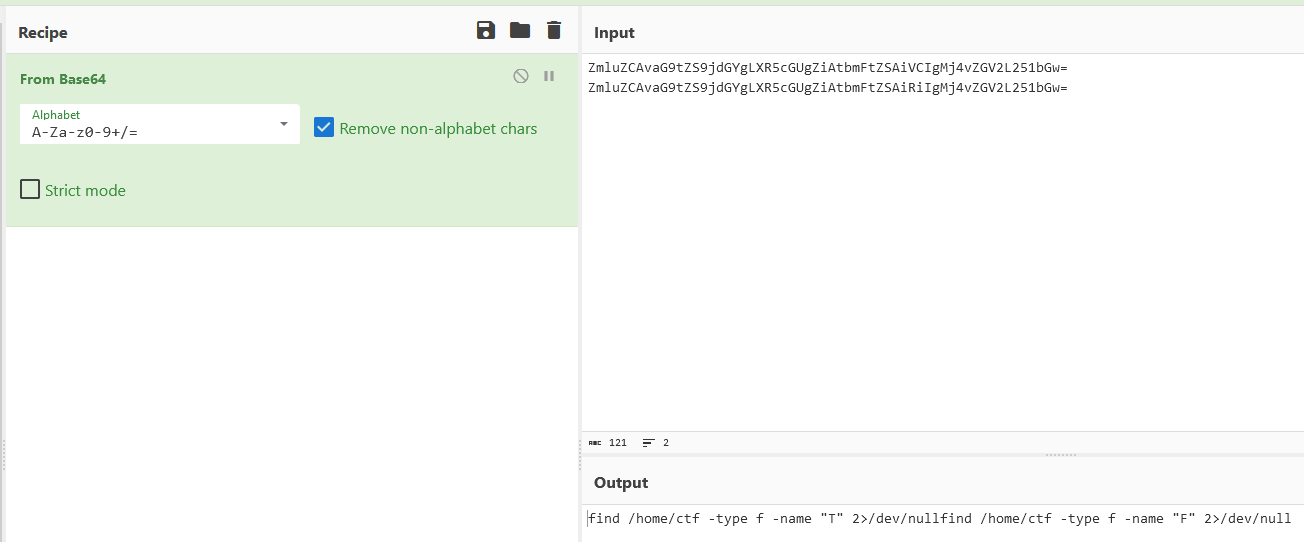
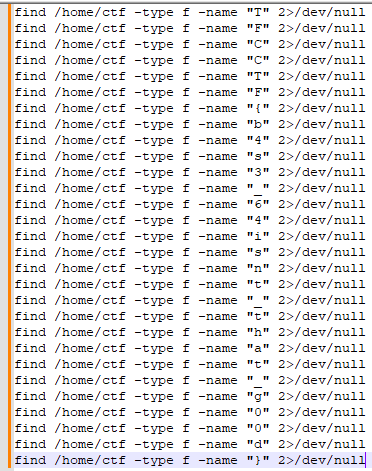
All these lines together give us the following:
Which when trimmed gives us the following result:
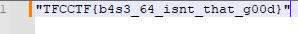
Which gives us our flag: TFCCTF{b4s3_64_isnt_that_g00d}
Tools and sources used:
- wireshark
- CyberChef