Anita Borg
This is a writeup of the reversing challenge Anita Borg from the CyberHeroines(https://cyberheroines.ctfd.io/) CTF
Level: Easy/Medium, Score: 200
Anita Borg (January 17, 1949 – April 6, 2003) was an American computer scientist celebrated for advocating for women’s representation and professional advancement in technology. She founded the Institute for Women and Technology and the Grace Hopper Celebration of Women in Computing. - Wikipeda Entry
Chal: Have the vision to solve this binary and learn more about this visionary
Author: TJ
Challenge files:
fLag_TRACE (Elf Executable)
Observations
Running the file we get the following output, prompting us for the flag. Entering a single a doesnt yield a lot of results.
If we try disassebmling the main function, we get a wall of text.
Solution
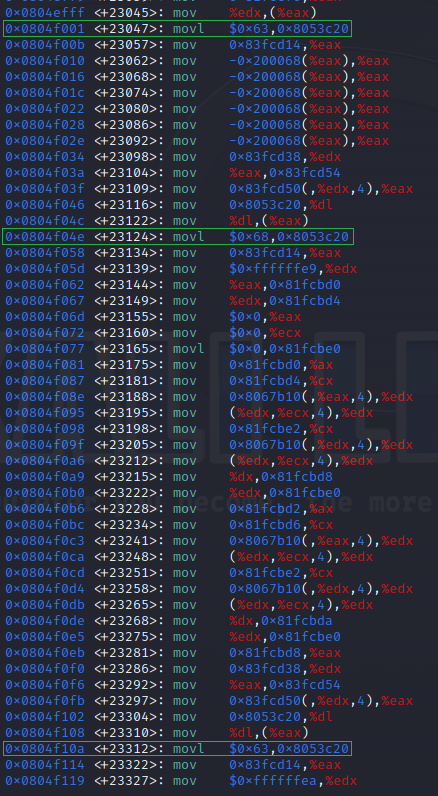
However, in this wall of text, if we’re patient enough, we can look at the instructions untill we find something interesting like here:
We have what appears to be some hex characters, the specific ones here are: 0x63 which resolves into c, 0x68 which resolves into h and 0x63 which resolves into c once again. This gives us chc which looks an awful lot like the first characters of our flag format: chctf{}
Very noteworthy here as well is the fact that they all move their characters to the address 0x8053c20. Knowing this address will be very useful.
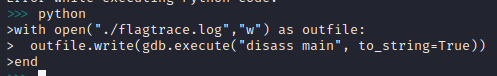
We can utilize python within gdb and save the output of our disass main command to a file, in this case one named flagtrace.log with the command seen here:
the code in text:
1
2
3
with open("./flagtrace.log", "w") as outfile:
outfile.write(gdb.execute("disass main", to_string=True))
end
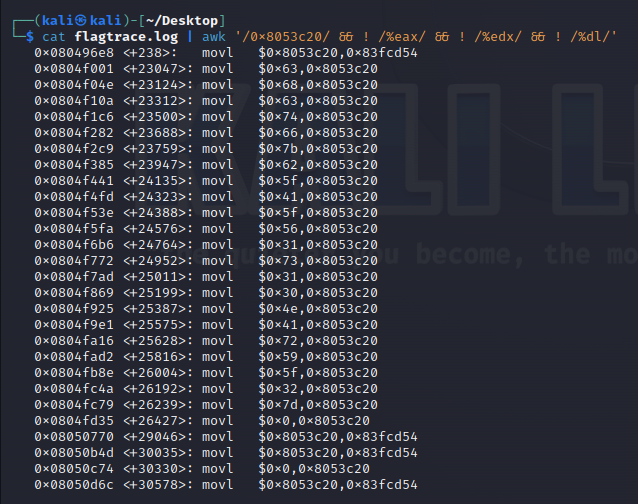
trying to cat out the contents of our flagtrace.log file, and grepping for our 0x8053c20 we get a better but still very messy result.
After experimenting around with filtering the output, I found a cohesive enough output with the command cat flagtrace.log | awk '/0x8053c20/ && ! /%eax/ && ! /%edx/ && ! /%dl/'. The result of this can be seen here:
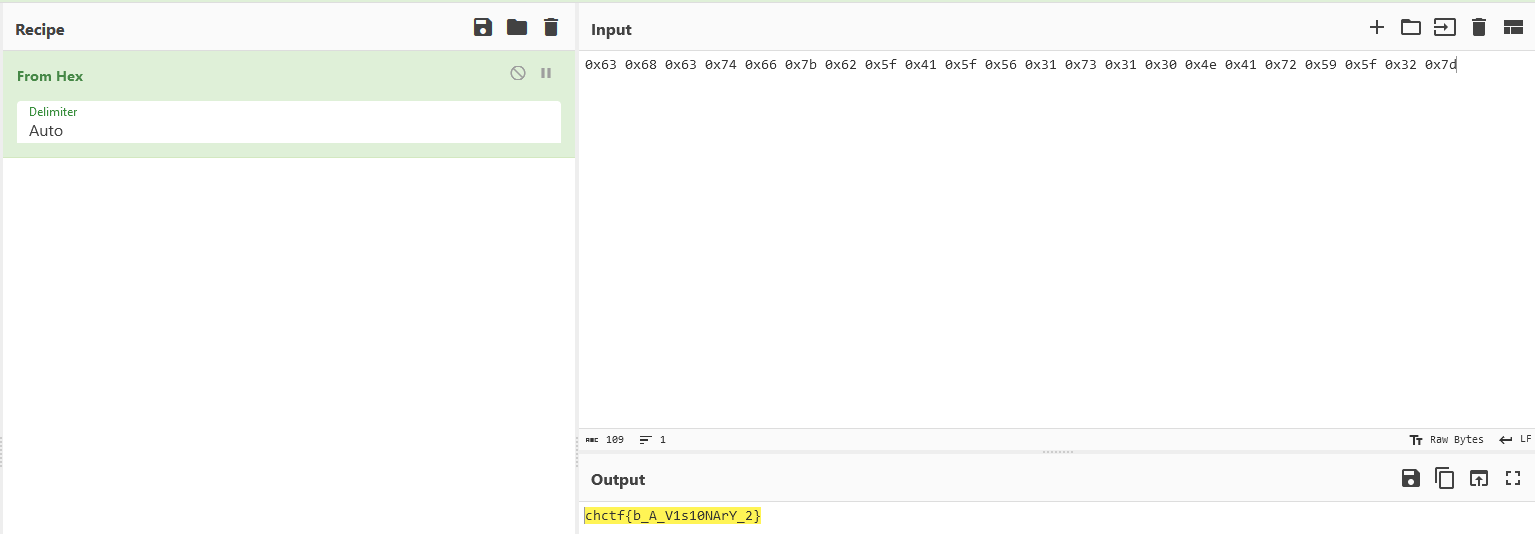
We’ve now found our characters: 0x63 0x68 0x63 0x74 0x66 0x7b 0x62 0x5f 0x41 0x5f 0x56 0x31 0x73 0x31 0x30 0x4e 0x41 0x72 0x59 0x5f 0x32 0x7d
If we use a tool like CyberChef we can decode these characters, as seen here:
Giving us our flag
chctf{b_A_V1s10NArY_2}
Tools used:
- gdb
- gdb dashboard from cyrus-and
- python (in gdb)
- awk
- CyberChef (or another hex decoder